Advanced Network Modification Techniques
As the demand for faster, more reliable telecommunications networks continues to grow, advanced techniques in network modification are essential for maintaining a competitive edge. These techniques go beyond basic upgrades and optimizations, leveraging cutting-edge technologies and strategies to deliver exceptional performance and scalability.
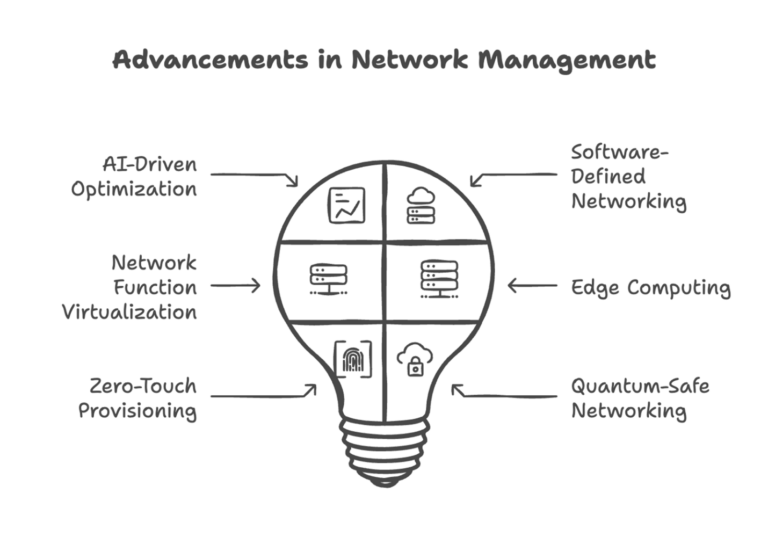
AI-Driven Network Optimization
Artificial intelligence (AI) is revolutionizing network management by automating processes and enabling predictive insights. AI-driven tools can identify inefficiencies, predict traffic patterns, and recommend adjustments in real time.
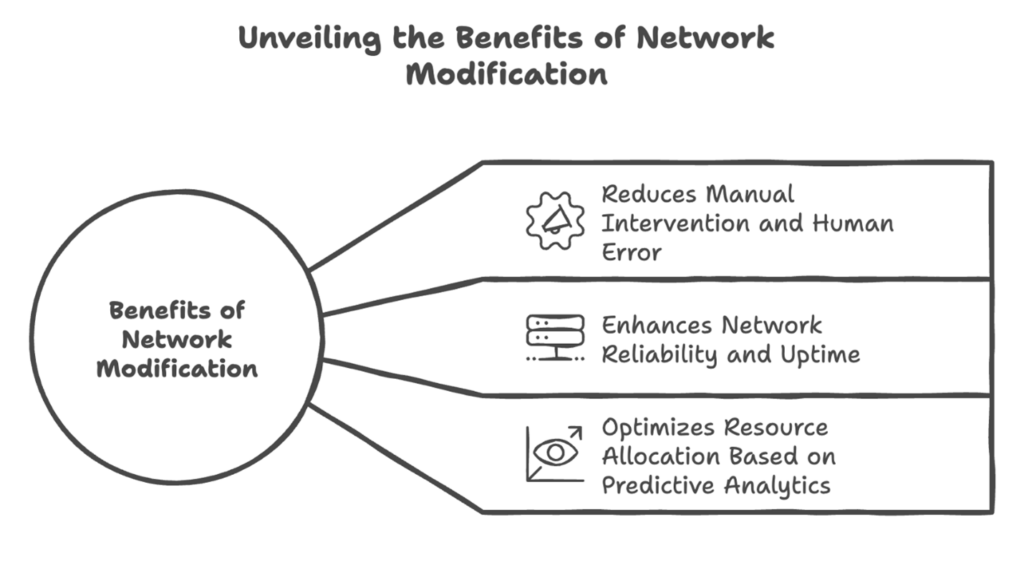
Benefits:
- Reduces manual intervention and human error.
- Enhances network reliability and uptime.
- Optimizes resource allocation based on predictive analytics.
Software-Defined Networking (SDN)
SDN separates the network control plane from the data plane, allowing for centralized management and dynamic configuration. This approach enables more agile and adaptable networks.
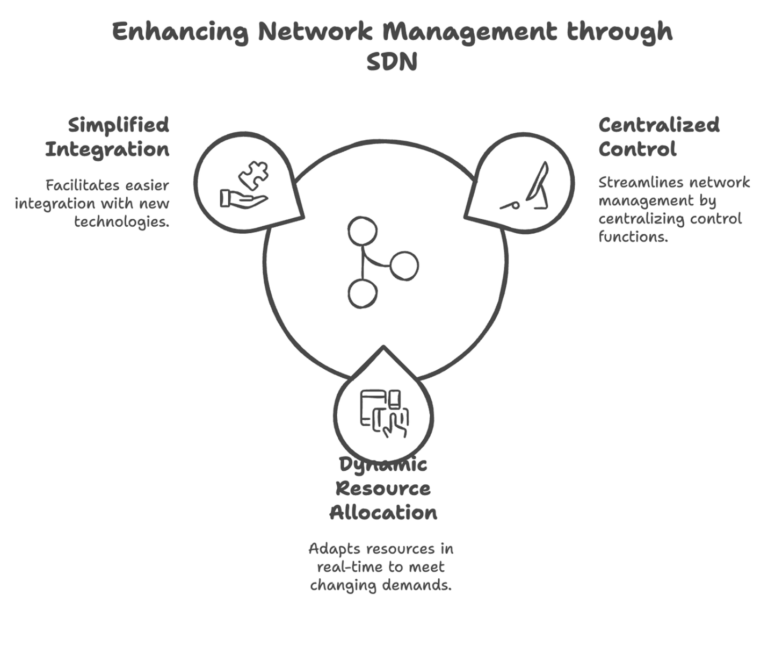
Key Features:
- Centralized control for easier network management.
- Dynamic resource allocation to meet changing demands.
- Simplified integration with new technologies.
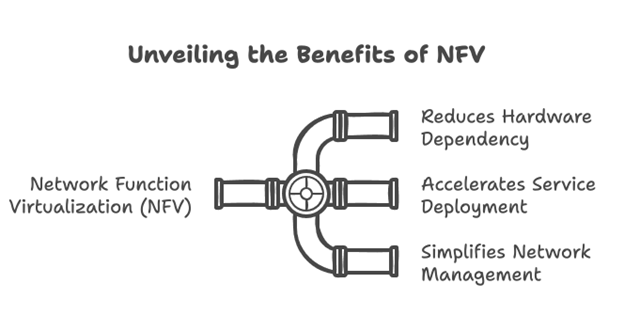
Network Function Virtualization (NFV)
NFV replaces traditional hardware-based network functions with software running on commercial off-the-shelf (COTS) hardware. This reduces costs and increases flexibility.
Advantages:
- Reduces dependency on specialized hardware.
- Accelerates deployment of new services.
- Simplifies network scaling and maintenance.
Example:
A service provider virtualizes its firewall and load balancer functions, enabling rapid scaling during high-demand periods without additional hardware.
Insight:
NFV adoption can reduce capital expenditures by up to 40% and operational expenditures by 20%.
Edge Computing Integration
Edge computing brings data processing closer to the source, reducing latency and improving performance for time-sensitive applications. This is especially critical for IoT and 5G networks.
Use Cases:
- Real-time analytics for connected devices.
- Enhanced gaming experiences with reduced latency.
- Improved performance for autonomous vehicles and smart cities.
Example:
A smart city deploys edge servers to process traffic data locally, enabling faster decision-making for traffic light optimization.
Fun Fact:
By 2025, edge computing is projected to handle 75% of all enterprise-generated data.
Zero-Touch Provisioning (ZTP)
ZTP automates the deployment and configuration of network devices, reducing the time and effort required for setup. This technique is particularly useful for large-scale deployments.
Benefits:
- Minimizes manual configuration errors.
- Speeds up network expansion projects.
- Improves consistency across deployments.
Example:
A telecom operator uses ZTP to roll out hundreds of new routers across multiple locations, completing the deployment in days instead of weeks.
Insight:
ZTP reduces configuration times by up to 90%, significantly accelerating project timelines.
Quantum-Safe Networking
With the advent of quantum computing, traditional encryption methods face potential obsolescence. Quantum-safe networking techniques, such as post-quantum cryptography, ensure long-term security.
Key Strategies:
- Implementing quantum-resistant encryption algorithms.
- Using quantum key distribution (QKD) for secure communication.
- Preparing networks for future quantum advancements.
Example:
A financial institution upgrades its network to include quantum-safe encryption, ensuring secure transactions for years to come.
Did You Know?
Organizations adopting quantum-safe strategies can future-proof their networks for the next 20+ years.
Additional Strategies to Explore
Intent-Based Networking (IBN)
IBN automates network operations by interpreting business intent and translating it into network policies. This ensures alignment between IT operations and organizational goals.
Blockchain for Network Security
Integrating blockchain provides a decentralized approach to securing data transmissions, reducing the risk of tampering or unauthorized access.
Pioneering the Future of Telecom Networks
Advanced network modification techniques are transforming the way telecom providers build and manage their infrastructure. From AI-driven optimization to quantum-safe networking, these innovations are paving the way for faster, more reliable, and future-proof networks.
By adopting these techniques, organizations can stay ahead of technological advancements, meet growing customer demands, and maintain a competitive edge in an increasingly connected world. To learn more about implementing these strategies, explore our Comprehensive Guide to Network Modification.

