Network modifications are critical for maintaining modern and efficient telecom systems. However, ensuring network modification compliance with industry regulations and safeguarding security during these modifications are significant challenges. Read with us as we explore the key compliance requirements, security risks, and strategies to address these aspects effectively.
Importance of Compliance in Network Modifications
Adhering to compliance standards is crucial for maintaining operational integrity, avoiding legal penalties, and ensuring customer trust. Understanding the key areas of basic network modification compliance helps organizations align their network modifications with industry regulations.
Key Compliance Areas
Key compliance areas focus on data protection, industry standards, and environmental guidelines. These elements ensure that network modifications are conducted responsibly and within the scope of legal frameworks.
Data Protection Regulations
Data protection laws such as GDPR and CCPA require networks to ensure user data remains secure during and after modifications.
- Implement robust encryption and access controls.
- Regularly audit data handling practices to ensure compliance.
Industry Standards
Telecom networks must adhere to standards such as ISO/IEC 27001 and PCI DSS to maintain operational integrity.
- Use certified tools and technologies.
- Engage with compliance experts during the planning phase.
Environmental Compliance
Upgrades and modifications should meet environmental guidelines to reduce waste and promote sustainability.
- Recycle old hardware responsibly.
- Opt for energy-efficient equipment during upgrades.
Addressing Security Risks During Modifications
Network modifications often expose vulnerabilities that can be exploited by cyber threats. Identifying common security risks and implementing proactive strategies is essential to safeguarding critical infrastructure.
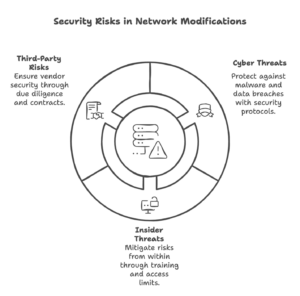
Common Security Risks
Understanding the various security risks associated with network modifications helps organizations prepare and defend against potential threats.
Cyber Threats
Modifications can expose networks to cyberattacks, including malware, ransomware, and data breaches.
- Implement multi-layered security protocols.
- Use intrusion detection and prevention systems (IDPS).
Insider Threats
Human errors or malicious activities from within the organization can compromise network security during modifications.
- Conduct regular employee training on cybersecurity best practices.
- Limit access to sensitive data and systems.
Third-Party Risks
Vendors and contractors involved in modifications can introduce vulnerabilities.
- Perform due diligence on third-party partners.
- Establish clear security guidelines in vendor contracts.
Strategies for Ensuring Compliance and Security
To achieve compliance and security during network modifications, organizations need a combination of advanced technologies, robust policies, and continuous monitoring. These strategies lay the groundwork for a secure and compliant network environment.
Implementing Compliance Tools
Compliance tools streamline the tracking and management of regulatory requirements, making it easier to stay aligned with industry standards.
- Use software solutions to track regulatory requirements and automate compliance reporting.
- Example: Tools like OneTrust and LogicGate simplify compliance management.
Regular Security Audits
Regular audits help identify and mitigate vulnerabilities, ensuring ongoing protection against emerging threats.
- Schedule periodic audits to identify vulnerabilities and address them promptly.
- Conduct penetration testing to simulate real-world attacks and evaluate defenses.
Encryption and Data Protection
Data encryption is a critical component of network security, safeguarding information in transit and at rest.
- Use end-to-end encryption to protect data in transit and at rest.
- Implement tokenization to secure sensitive data.
Collaborating with Experts
Partnering with experienced professionals ensures that compliance and security measures are effectively integrated into network modification projects.
- Engage with compliance consultants and cybersecurity specialists to address complex challenges.
- Example: Partner with firms experienced in telecom compliance and security.
Real-World Example: Ensuring Compliance and Security
Real-world examples demonstrate how organizations can successfully address compliance and security challenges during network modifications.
Case Study: Large-Scale Network Upgrade
A major telecom provider undertook a large-scale network upgrade to integrate 5G capabilities. By prioritizing compliance and security, they:
- Achieved ISO/IEC 27001 certification during the project.
- Implemented AI-driven security tools to monitor threats in real-time.
- Reduced compliance-related risks by 30% through automated reporting tools.
Navigating Compliance and Security Challenges with Confidence
Compliance and security are integral to the success of any network modification project. By understanding regulatory requirements, addressing vulnerabilities, and leveraging advanced network modification tools and expert guidance, organizations can ensure their networks remain robust, secure, and compliant.
Explore more strategies for achieving compliance and security in our Comprehensive Guide to Network Modification.

